
In this post, we’d like to address some interesting points outlined in David Solove’s “.” One area that absolutely must be addressed is the lack of proper risk assessments.
Two-thirds of all entities–47 of out of 59 providers, 20 out of 35 health plans, and 2 out of 7 clearinghouses—had no complete or accurate risk assessment program.
If you don’t conduct a suitable risk assessment, how can you possibly be aware of your vulnerabilities? How could you even hope to protect your business, your clients, and your partners? If that isn’t frightening enough, Solove also states that
The 2014 audits will focus on covered entities and the following areas: security risk analysis and management, breach notifications, and privacy notices and access issues. The focus will shift to business associates in 2015, particularly on security risk analysis and management and breach reporting to covered entities.
Improving your organization’s risk assessment functionality just jumped to the top of your priority list.
Read: Risk Management Today: What’s Wrong with This Picture?
However, there is little or no point in conducting a risk assessment that isn’t currently part of, or going to be part of a larger risk management program. The spirit of conducting a risk assessment is to demonstrate that you understand your risks, are making appropriate decisions based on your risks, and that you have a mechanism in place to continually track risks against a changing business environment. A Risk Assessment is single task you perform within a Risk Management program. It may say “Risk Assessment” on your checklist, but without ongoing Risk Management to back it up you will have a difficult time defending yourself in an audit or investigation.
4 Components of Risk Management
There are four components to Risk Management – Framing, Addressing, Responding, and Monitoring.
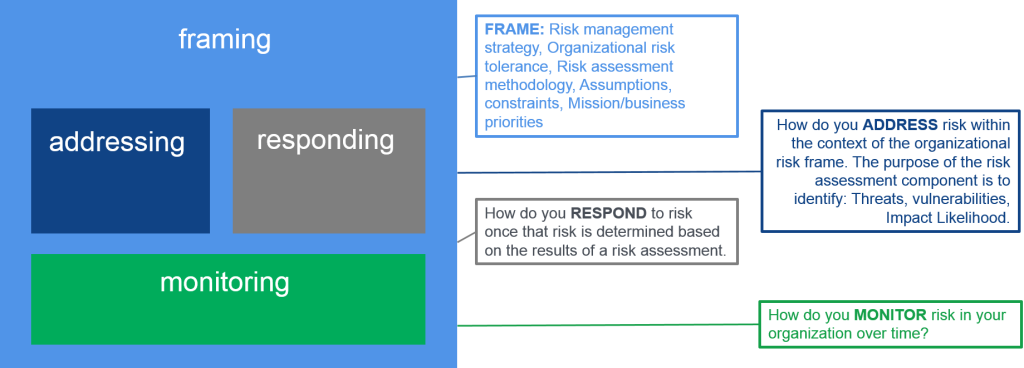
Framing Risk
The first component of risk management addresses how organizations frame risk or establish a risk context. As a result of analyzing and understanding the risk context, the business will outline the risk management strategy, organizational risk tolerance, risk assessment methodology, assumptions, constraints, and mission/business priorities.
Addressing Risk
The second component of risk management addresses how organizations assess risk within the context of the organizational risk frame. The purpose of the risk assessment component is to identify:
- Threats to the organization (i.e., operations, assets, or individuals) or threats directed through organizations against other organizations
- Internal vulnerabilities, such as information systems, business processes, and enterprise architecture, and vulnerabilities that are external to organizations, like supply chain activities and external service providers.
- The harm or adverse impact that may occur given the potential for threats exploiting vulnerabilities
- The likelihood that harm will occur. The end result is a determination of risk (i.e., typically a function of the degree of harm and likelihood of harm occurring).
Responding to Risk
The third component of risk management addresses how organizations respond to risk once that risk has been identified, based on the results of a risk assessment. The purpose of the risk response component is to provide a consistent, organization-wide response to risk in accordance with the organizational risk frame. The risk response is achieved through these activities.
- Develop alternative courses of action for responding to risk.
- Evaluate the alternative courses of action, and determine which is appropriate based on organizational risk tolerance.
- Implement the chosen risk responses. When risk cannot be avoided, a risk response almost always involves the implementation of one or more controls.
Monitoring Risk
The fourth component of risk management addresses how organizations monitor risk over time. The purpose of the risk monitoring component is to:
- Determine the ongoing effectiveness of risk responses (consistent with the organizational risk frame). This involves validating that controls are selected, designed and operating effectively over time. In other words, validate that controls are effective at reducing risk.
- Identify risk-impacting changes to organizational information systems and the environments in which the systems operate. Be sure to have processes to refresh risk assessments when risk impacting changes occur.
- Identify deficiencies and correct them.
Use a Third Party for your Risk Assessment
Finally, we recommend using a 3rd party to conduct your risk assessment for a few reasons:
- If this is your first risk assessment or you do not currently have a risk management program in place, 3rd party experts can help you make sure your assessment is appropriately scoped, that the appropriate skills and rigor are applied to the assessment, and can provide the recommendations you need to start building your risk management program.
- If you have to provide proof to a customer or an authority that you’ve preformed a risk assessment, having a non-biased 3rd party perform that assessment is the most direct and reliable way to meet the requirement. It is not unheard of, for organizations with extremely mature risk management capabilities successfully meet the risk assessment requirement using internal resources; however this is definitely the exception.
- Lastly, risks assessments get into everyone’s business. It is often difficult to navigate politics, silos, and infighting and get down to the real risks your company is carrying. If you’re new to risk management, having a 3rd party perform the assessment can give a more accurate picture of your overall risks without people feeling like they’ve been personally exposed by their co-workers.
Read: Contract Negotiation Checklist – Don’t forget Your Pre-Nup
To maximize the effectiveness of your efforts, you should plan on conducting a comprehensive risk assessment of the enterprise, key business processes, and information systems at least once a year. Then as part of your on-going risk management program you can perform self-directed internal risk assessments with narrower departmental focus to measure progress over the course of the year.
Now that we’ve covered the big picture of risk management, we’ll get back to risk assessments in our next blog.
We’ve addressed other stats from David Solove’s article in Re-Thinking Security & Privacy Training.
